

| Career Prospects | Further Studies | Course Overview |
|---|---|---|
| Cybersecurity Track, Security Analyst, Penetration Testing Analyst | Opens doors to pursue a degree at reputable local and overseas universities. PSG University, Dortmund of University, Palance University |
Being able to protect computer operating system, networks and data from all the vulnerabilites in cyber attacks, learning to moniotr and keeping a lookout if hacker entered the unauthorised system they will be ban and fines. Having to learn all this it will be great future in the IT world as it could have company employing you to protect their organisaztion server and systems. |
[FortSIEM]
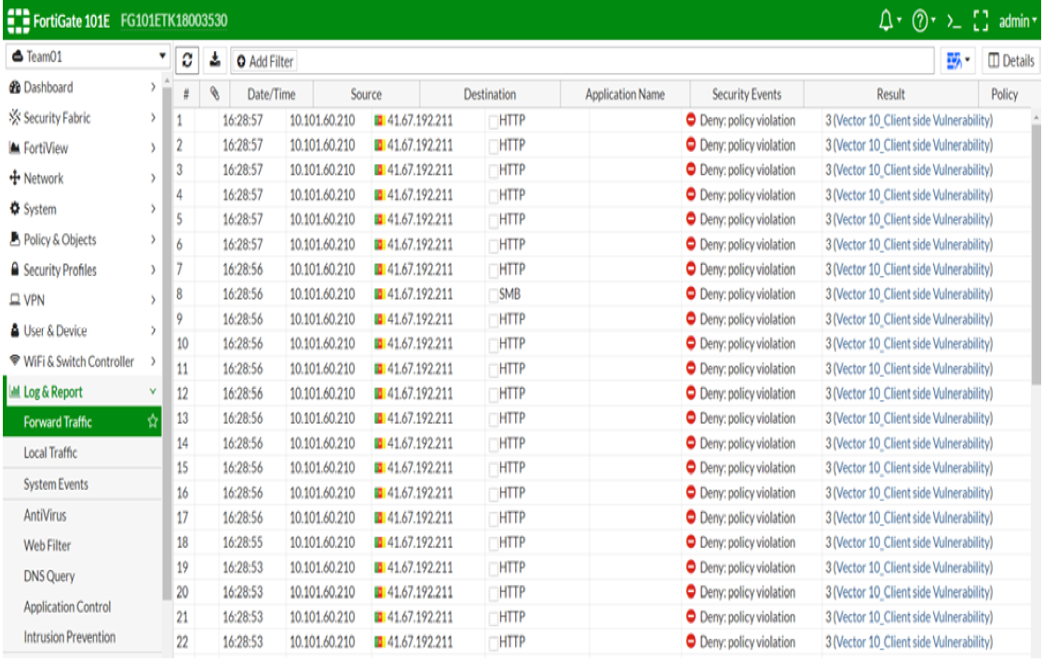
A firewall rule that was set to block the traffics from the single source of the traffic
[FortiGate]
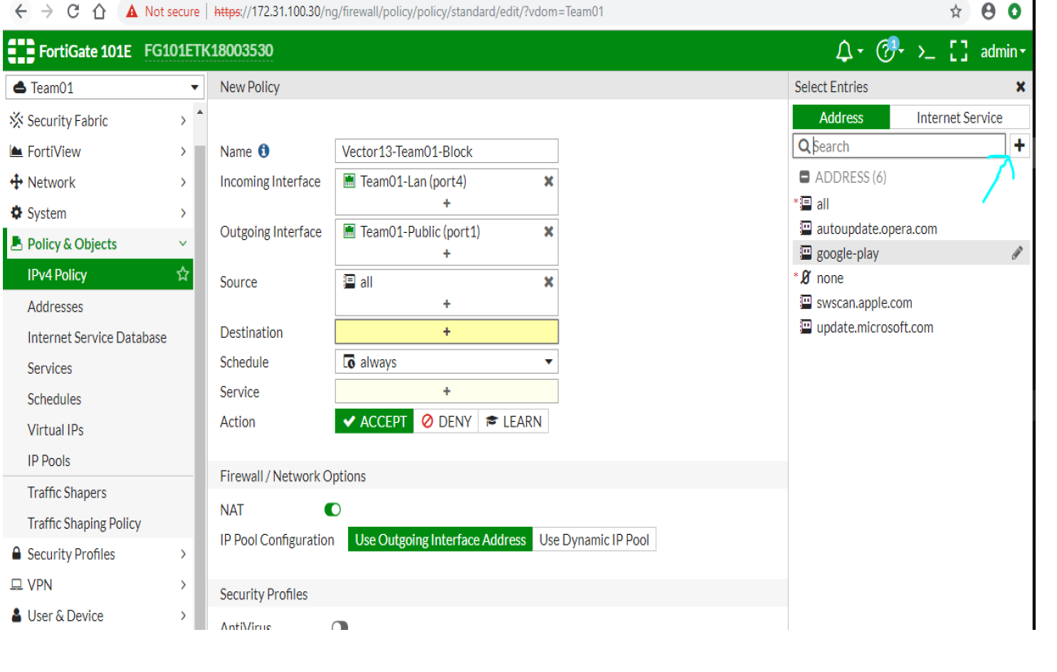
Creating a rule inside the Fortnet Firewall
[CyberTest System]
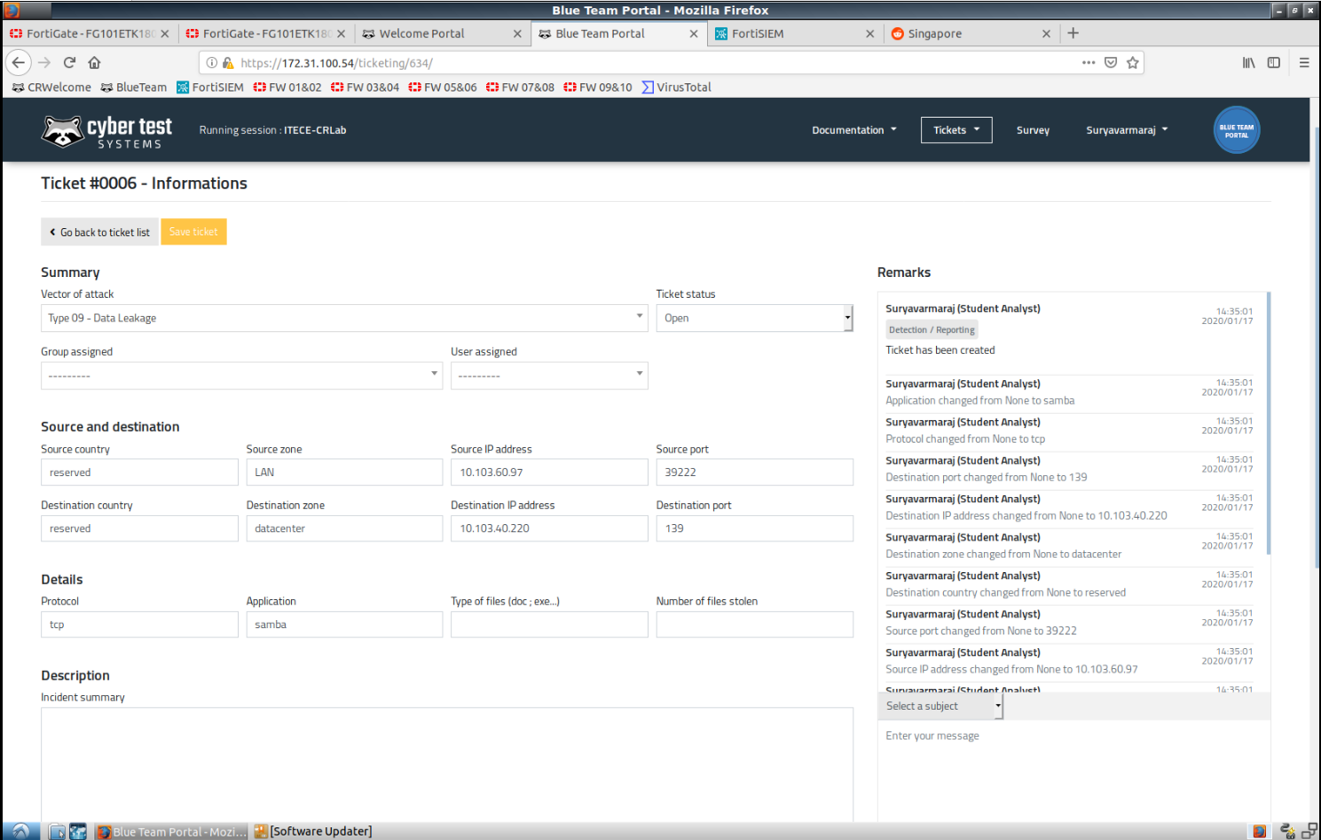
Having tickets record of methodologies and issues tactics to measure how effective the potential attacks
[FortiGate]
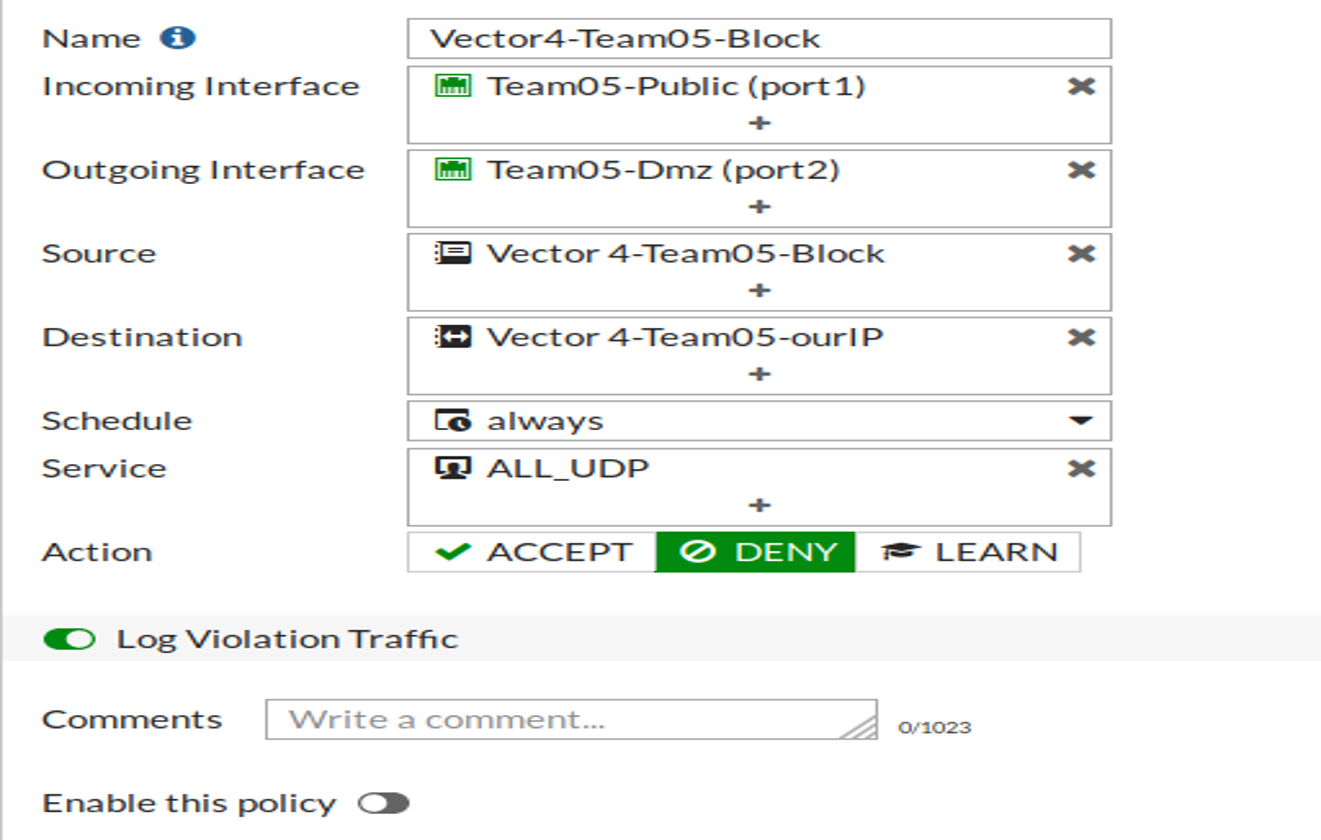
Creating a policy to have permission on the incoming interface, outgoing interface as well as the IP Address of the Source/ Destination address. Configuring the policy to only allow service from "ALL UDP"
[Link Control Protocol Tools]
By using the LCP tool learn to crack administrator passwords, the program aduits user account password and recover them all in the operating system windows 2003. With the tools it can used to recover lost passwords and test password security.
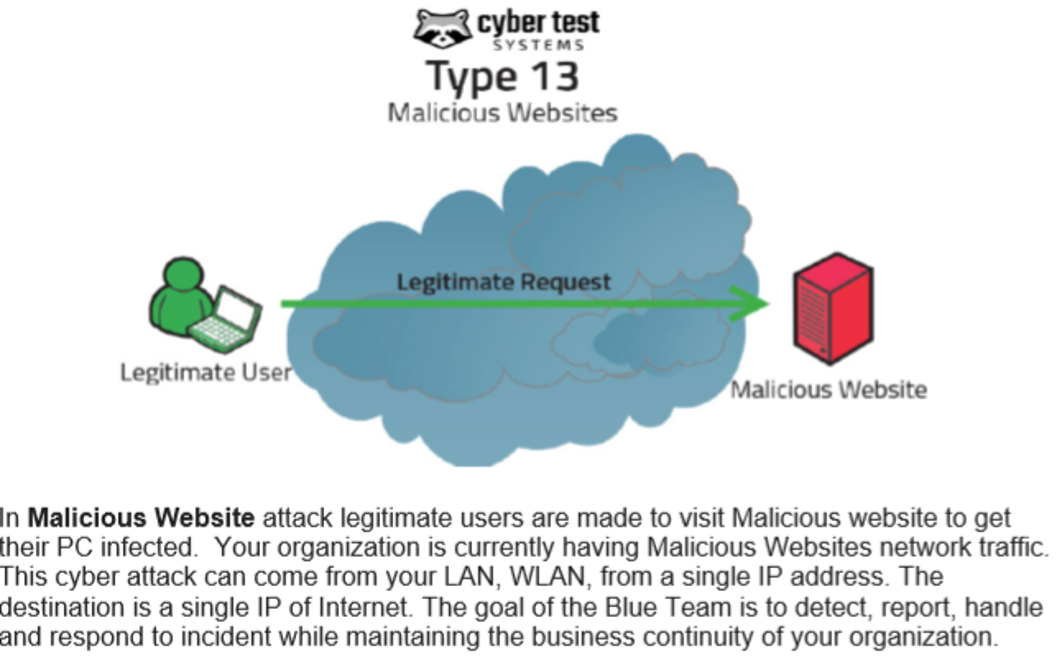
[CyberTest Systems]
After learning to use tools in the CyberTest System we are require to detect, report, handle and respond to the incident. This is one type of cyber attack that student will get to encountereed and solve the issues.

• Cloud Computing Security
• Cybersecurity Attack & Defense
• Cybersecurity Operations & Intelligence
• Mobile Security
• Operations Security
• Advanced Cyber Attack Forensic Techniques
• Cyber Forensic Process
• Disaster Recovery & Finance Continuity Management
• Malware Analysis
• Entrepreneurship
• Foundation of AI
• Robotic Process Automation
• Social Media Analytics
• Discover how to bulit the services and networks, and keep them from cyber attack and safe from hacker.
• Write programs to connect sensors and software, so as to develop smart solutions for various organisaztion and industry such as healthcare, transportation and retail.


Kali Linux
One of the most common cybersecuirty OS that contains up to 300 different tools for security auditing. It provides organization various tools like scanning network and IT systems for differnet vulnerabilities.
Click Here to learn more about Kali Linux

Metasploit
Metasploit contain very impressive collection of different tools with things like penetration testing exercise. With CyberSecurity Professionals and IT Experts use Metasploit to accomplish task and secuirty objective.
Click Here to learn more about Kali Linux

Wireshark
Formely was known as "Ethereal" it is a console based cybersecuirty tools. It is an tools used to analyse network protocol and analysing network secuirty system in real time. Wireshark analyse network infrastructure and sniff the network in real time asses.
Click Here to learn more about Kali Linux